Q: How do I stop my Tasks prompting for database passwords?
Welcome to the latest Studio 3T Ask Manatees Anything – #Studio3T_AMA. Want to know how to use Studio 3T to make your MongoDB life better? Just tweet and use #Studio3T_AMA or email [email protected].
A: For a Task to run unattended, it needs to be able to make its database connections without any user intervention. You can configure a connections to a databases in the Connections Manager to use a saved database password. If you leave the field blank, Studio 3T will prompt for a database password from the user when connecting. It’s that latter case that causes a Task to need user input.
The simple solution to this, is to save a password with the connection the task. You set this in the Authentication tab of the Connection Manager. By setting the password in the Authentication tab, the connection is usable without user intervention. Studio 3T saves these passwords using our own default encryption system.
Adding A Master Password
If you want to ensure that only authorised users have access to the connections with passwords, enable the cryptographic key store in Studio 3T. This adds a layer of defence by using a master password to encrypt stored keys (and passwords). You will then have to enter the master password when you start Studio 3T. Without the master password, Studio 3T will not be able to decrypt saved database passwords.
Using the cryptographic key store is also useful for situations where you want to control access to the credentials stored in Studio 3T. It helps ensure only users with the master password can start and use the application.
You can enable the cryptographic key store when installing Studio 3T for the first time, or from Studio 3T’s preferences. Studio 3T will decrypt passwords to make use of them. This means that saved passwords can be made visible when exporting MongoDB connection strings. By default, passwords are omitted from connection strings.
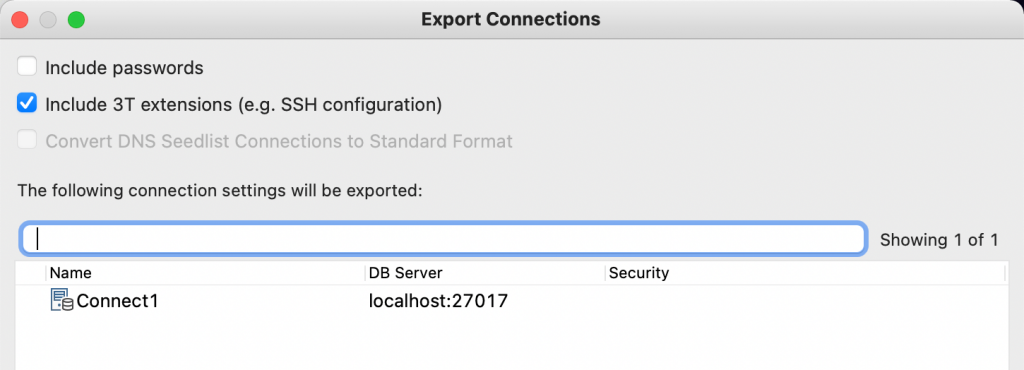
If you do want to include the stored passwords, you will have to select the option at the top of the Export Connections dialog. This also applies to the Export URI option:
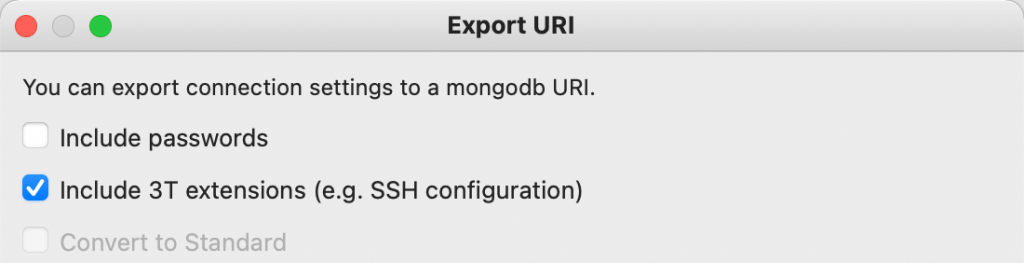
As you can see, this makes accidental leakage of passwords much less likely.
If you consider this is still an issue, consider configuring your MongoDB to use certificate-based authentication to avoid this particular possibility. For most client side operations, securely storing the passwords and only extracting them when needed is an effective strategy.