Studio 3T offers a cryptographic key store to control access to credentials, ensuring that only authorized users have access to MongoDB connections with passwords. The cryptographic key store provides an extra layer of security by using a master password to encrypt stored keys and passwords. Only users with the master password can start and use Studio 3T.
For most client-side operations, securely storing passwords and extracting them only when needed is an effective defense strategy. However, if this is insufficient for your security requirements, consider configuring your MongoDB deployment to use certificate-based authentication instead.
Setting up the cryptographic key store
When you set up Studio 3T you can choose between the default password encryption or the cryptographic key store.
With default password encryption, Studio 3T encrypts passwords before storing them when you set up a connection in the Connection Manager.
The cryptographic key store provides an extra layer of security by requiring you to enter a master password every time you start up Studio 3T. The master password allows Studio 3T to decrypt the stored database passwords when connecting to MongoDB.
You can switch between the default password encryption and the cryptographic key store in Preferences > Advanced settings > Security.
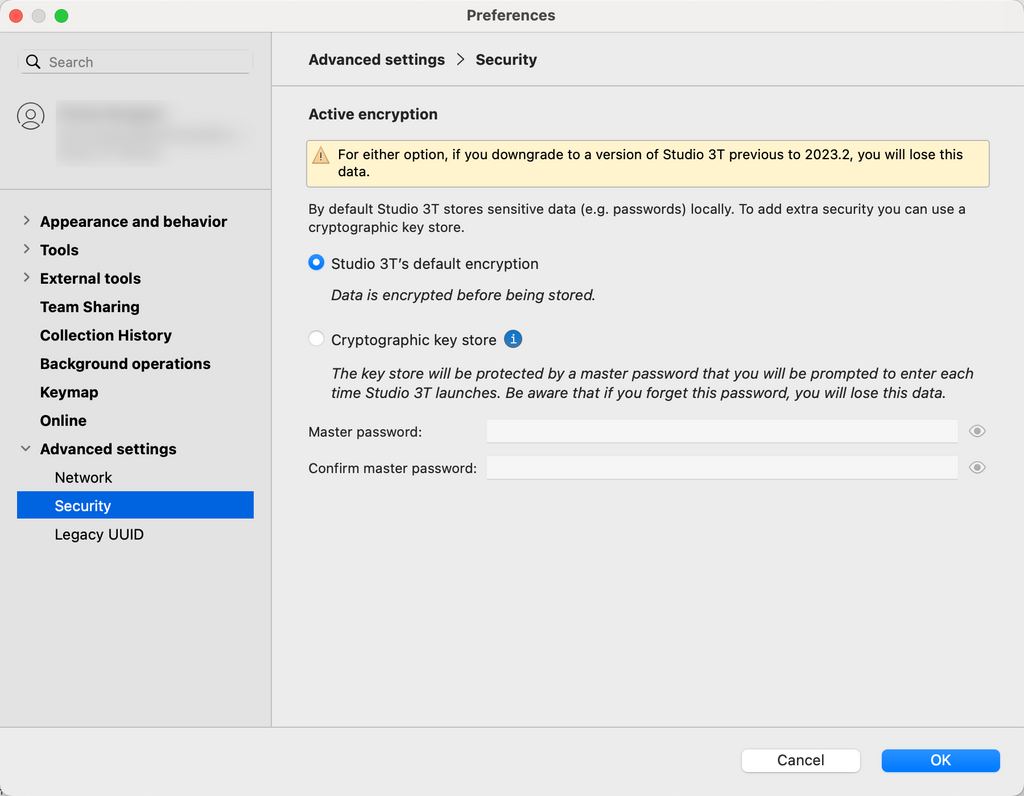
When you switch to the cryptographic key store, Studio 3T imports all your connections into the cryptographic key store. The files that previously stored the connection details are deleted to ensure that they are no longer accessible.
Learn more about the different authentication mechanisms in the MongoDB documentation.
This article was originally published by Kathryn Vargas and has since been updated.