What is data masking?
Data masking protects sensitive information from those who don’t have the authorization to see it. It secures the file transferring process from one location to another. It also helps to secure application development, testing, or CRM applications. It allows its users to access more realistic data for testing or training purposes.
Data masking can be done either statically or dynamically. Static data masking permanently replaces sensitive data by altering data at rest, while dynamic data masking shields private data in real-time and leaving the original at-rest data intact and unaltered. When a query is directed to a database, the records are replaced with dummy data, and then masking procedures are applied to it accordingly.
What types of data can be masked?
The types of sensitive data that data masking works on shielding are:
- Personal Identifiable Information (PII)
- Protected Health Information (PHI)
- Primary Account Numbers (PAN)
- Other sensitive information
Why use data masking?
Data masking tools may be used during application development or testing where apps require data input from an end-user. Data masking tools generally provide the following features and capabilities:
- A range of masking techniques available on-demand
- Centralized management of masking policy, audit trail
- Track compliance with data privacy law
- Apply masking rules code-free
- Apply different rules for subsets of data
- Access to data stored in various databases
- Share subsets of masked data on-demand
- Realistic but fictional data available for testing, known as “sandboxing”
Here are the best data masking tools for MongoDB to choose from to protect your data.
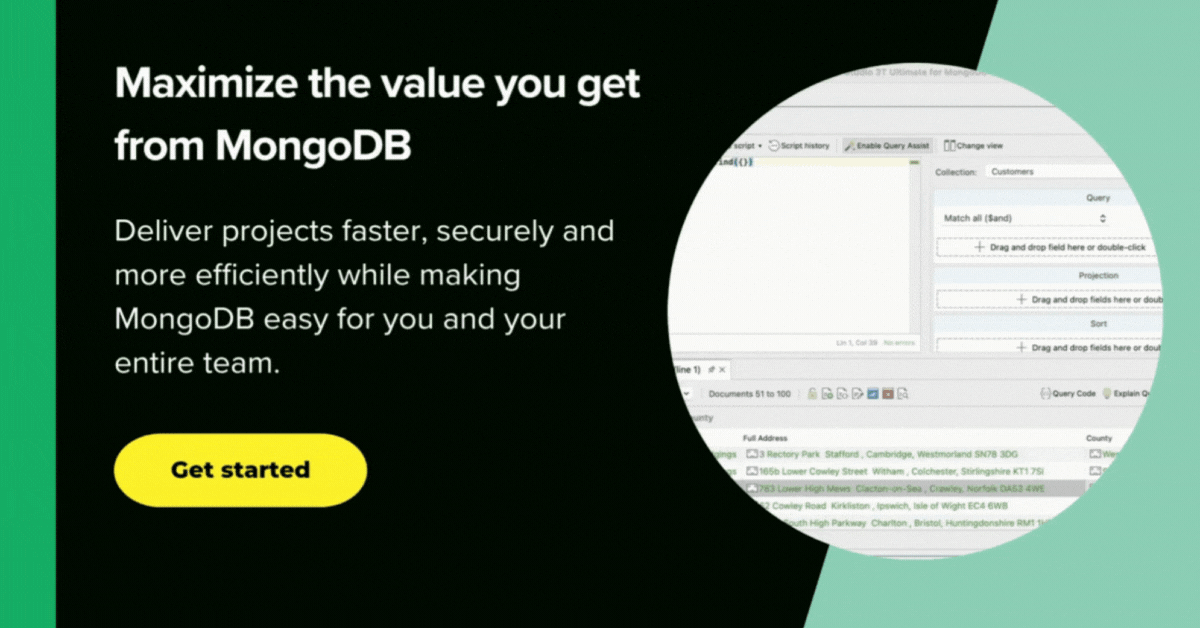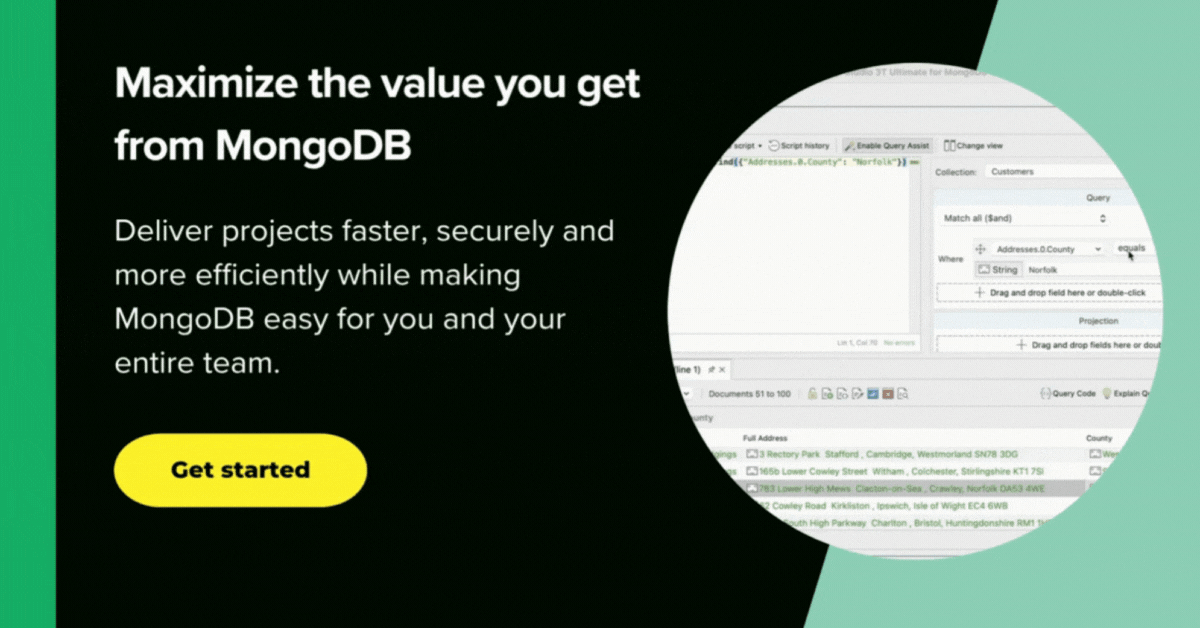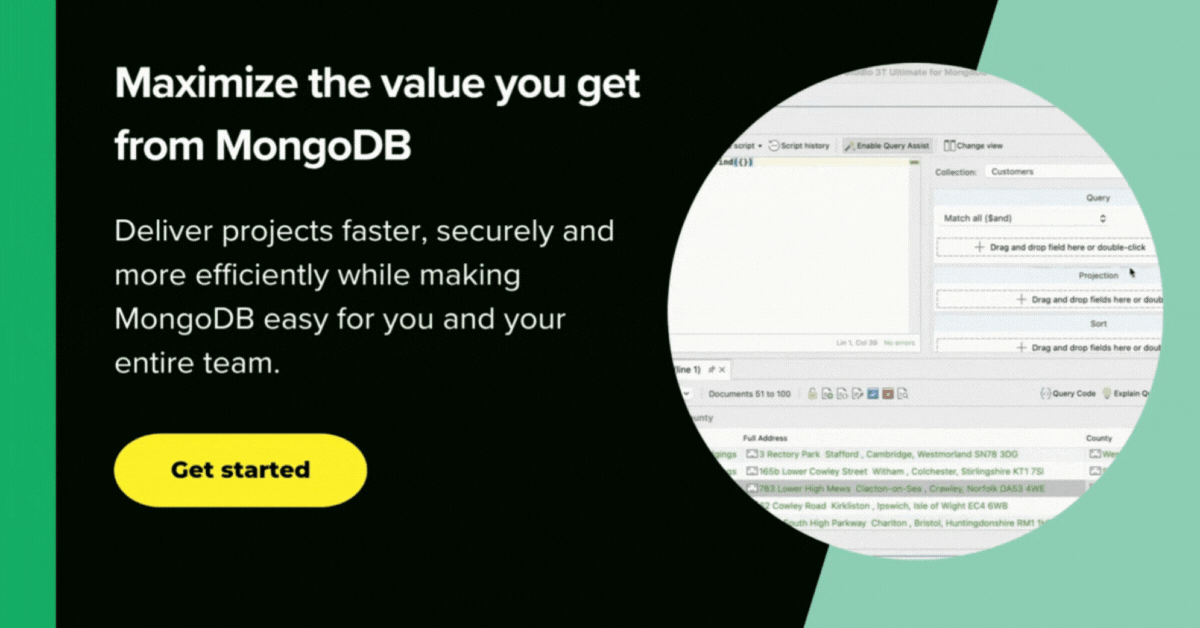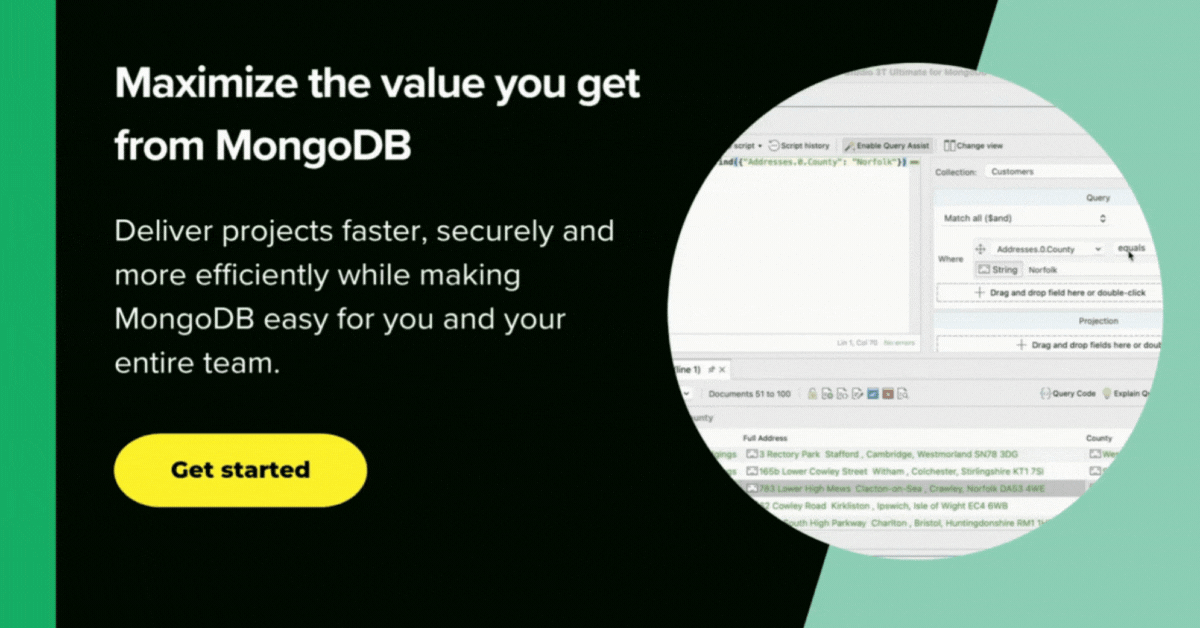
1. Studio 3T
Data Masking for MongoDB is the data masking tool in Studio 3T Ultimate that lets you obfuscate collections on a field level.
You can mask entire collections and decide which fields should be obfuscated and how. The masked documents are saved to a new collection by default, but you can also choose to overwrite the source collection.
You can apply a data masking technique to each field in a source collection, and choose whether to overwrite the source collection or export the masked documents to a new target collection.
It ensures that you remain compliant when dealing with sensitive data, whether you’re pushing production data to a lower environment or sharing exports with other teams or clients.
Source: Data masking in Studio 3T
Studio 3T also allows you to choose the right masking method for each field value.
| Field type | Data masking techniques |
| All field types |
*These three data masking techniques are the only options for Binary, Regex, Reference, Code, Min key, Max key, Mixed, Symbol, Timestamp, Undefined, and Unknown types. |
| String |
|
| Numeric | Includes Double, Int32, Int64, and Decimal128 types.
|
| Date |
|
| Array |
|
| Boolean |
|
| ObjectId |
|
2. IRI
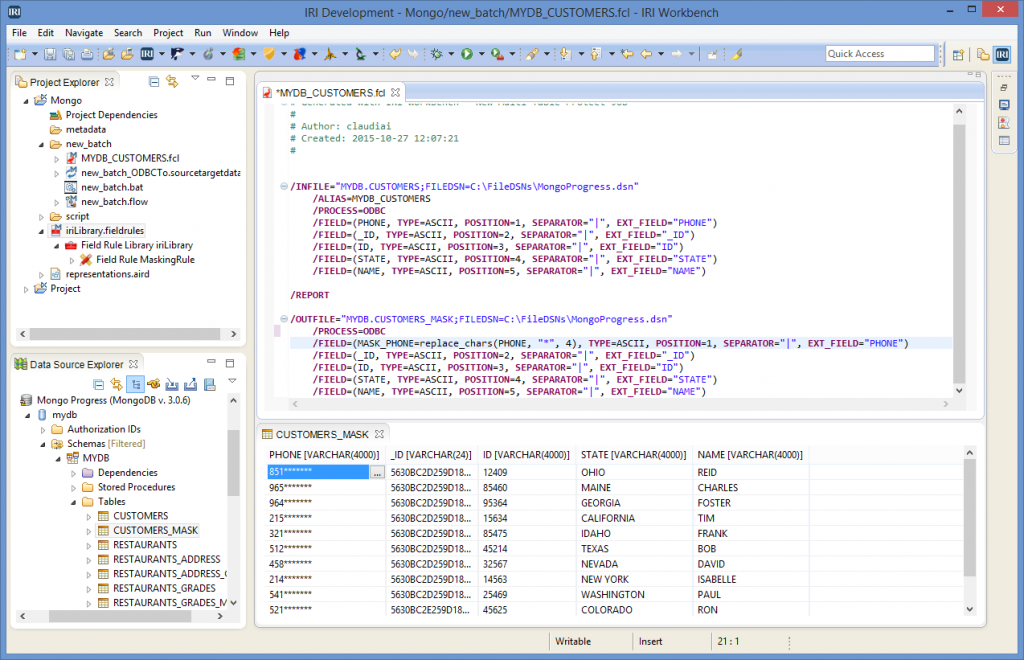
Source: IRI
The security software from IRI has a wide range of breach nullification, privacy law compliance, and DevOps (test data) environments. You can use IRI data shield products (or all of them in the IRI Voracity data management platform) to find and mask sensitive data deterministically on-premise or in the cloud, and to prove that you protected it.
The IRI products that provide static data masking functionalities are IRI FieldShield, IRI CoSort, and IRI Voracity. The field/column masking functions let you choose to blur, encrypt, hash, pseudonymize, randomize, redact, scramble, tokenize, etc.
| IRI FieldShield | classifies, finds, masks, and audits PII in a structured file, database, or HDFS sources |
| IRI DarkShield | classifies, finds, masks, and audits PII in unstructured files, documents, and images |
| IRI CellShield | classifies, finds, masks, and audits PII in Excel sheets, local or LAN-wide |
| IRI DMaaS | performs data masking as a service, including PII discovery and post-fix audits |
| IRI RowGen | creates realistic and referentially correct test data in DBs, files, and reports |
3. DataSunrise
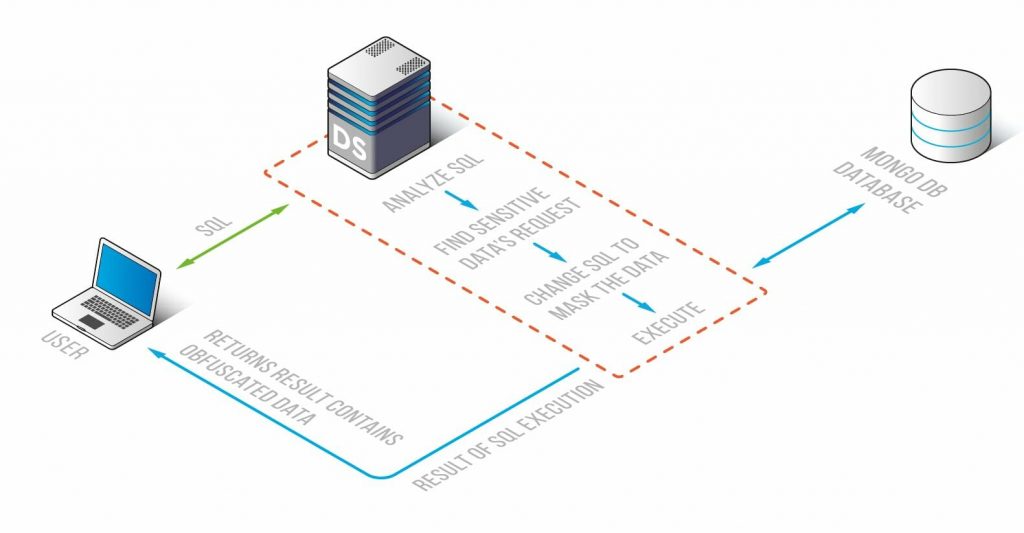
Source: Datasunrise
MongoDB Data Masking from DataSunrise aims to protect a database against data leaks and to make it impossible for unwanted users to read information from a MongoDB database.
This is achieved through dynamic obfuscation. The tool replaces real data in the database with random signs and values, hence making information impossible to read.
It intercepts all queries directed to your database and masks them based on your rules so that when they reach the MongoDB database, the requested information is already masked. So, unauthorized users can have access to the database for specific purposes like QA, application development, analytics, statistics, etc., but can’t see the sensitive and confidential information contained in it.
4. Informatica
Informatica has two data masking products:
- Dynamic Data Masking – Masks data when accessed by users without changing the original source data.
- Persistent Data Masking – Masks data in place or when copied to test, support, or outsource environments.
Informatica Dynamic Data Masking (DDM) masks or blocks sensitive information to users based on their role, location, and privileges.
You can specify criteria to identify which statements or results should be modified. When there’s a match, DDM applies one or more actions (e.g., mask, scramble, hide, rewrite, block, or redirect) to prevent unauthorized users from accessing sensitive information in real-time.
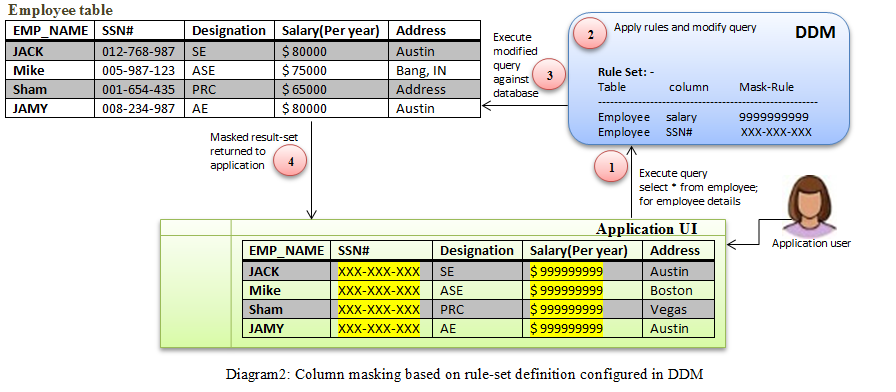
Source: Informatica
Informatica Persistent Data Masking (PDM) masks test or development data sets created from production data, regardless of the database, platform, or location. DDM provides alerts for unauthorized access attempts and includes logs for compliance and audits.
Informatica PDM provides pseudonymization of analytic data with encryption transformation, supporting needs for reversible masking for analytics or privacy needs. Format preservation during encryption ensures that the application data model stays the same.
Learn more about the data masking, data subset, data discovery, and data generation operations that you can perform on the MongoDB data types here.
Data masking, obfuscation, or anonymization is required when certain personally identifiable information (PII) or other sensitive data must be kept private. Hence choosing the right tool to help you handle data with peace of mind, protect your production data, keep your environments fresh, and obfuscate on demand is very important. We hope these tools take you one step closer to securing your MongoDB data.
Here’s a quick summary of the data masking tools mentioned above:
| Feature | Studio 3T | IRI | DataSunrise | Informatica |
| Platform Connectivity | MongoDB | All RDBMS & Top NoSQL DBs, Mainframe, flat and JSON files, Unix. | MS SQL Server, Azure SQL, AmazonRedshift, PostgreSQL, MySQL, MongoDB, and others. | Relational DB, Cloud Platforms. |
| Free trial | Yes | Yes | Yes | Yes |
| Dynamic Data Masking | — | Yes | Yes | Yes |
| Static Data Masking | Yes | Yes | Yes | Yes |
| Supports heterogeneous platforms such as Windows, Linux/Unix, Mac, Z/OS, etc. | Yes | Yes | Yes | Yes |
| Data redaction | — | Yes | Yes | — |
| Tokenization | — | Yes | Yes | — |
| Format-Preserving Encryption (FPE) | — | Yes | — | — |
| Provide templates and predefined rules | Yes* | Yes | — | Yes |
| Monitoring and compliance reporting such as GDPR, PCI DSS, HIPAA, etc. | Yes | Yes | Yes | Yes |
| Pricing | $699 per year per user | between USD $4,000 and $40,000K | As IaaS on AWS $15,000 per year | Need to contact Sales |
| Automation/Scheduling | Yes | — | — | Yes |
| Field-level data masking | Yes | Yes | Yes | Yes |